A damaging government leak exposes the real cost of budget tools in critical publishing roles
When a government body accidentally leaks market-sensitive data, the instinct is to blame human error - but what if the real culprit is the technology it has chosen?
It’s not often we get to write about a juicy political scandal involving a publishing system, especially one in which the cause of the scandal is so basic as to reinforce everything that we, as professionals in the space, say about what a publishing system should be when your business depends on it. Or, in this case, your job.
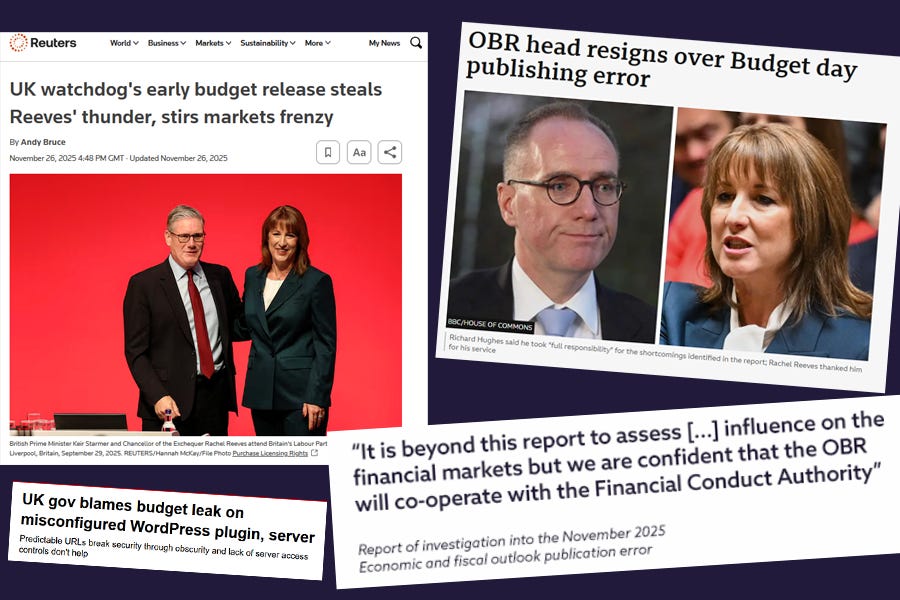
The scandal here is the accidental publication online of critical financial data underpinning the official announcement of the UK’s national Budget, last week, nearly an hour prior to the formal speech made in Parliament by the Chancellor of the Exchequer. In simple terms, the annual report for UK Plc was released early, and state-level and market-defining information was revealed before it should have been. This is no small thing. This is international financial market moving stuff.
The Office for Budget Responsibility’s premature release of its November 2025 Economic and Fiscal Outlook was clearly not the result of recklessness or incompetence. A rapid and thorough investigation conducted within days shows a team working under intense pressure, using widely adopted tools, and following what would be considered normal practice across much of the public and private sector. It’s worth reading the report to see how much of the timeline of events is recognisable to sites and content teams of all sizes in publishing and media.
And yet the outcome was serious. Market-sensitive information was accessible ahead of schedule, and trust was damaged. The organisation’s credibility took a hit through no malicious act, forcing its Chairman to resign within days and heaping embarrassment on the Chancellor and Prime Minister - the two most senior offices of state.
The sad part is, the root cause was not human error in the usual sense. It was structural, driven by the choice of platform, and cut to the heart of why specialist tools even exist in a world where so many tools claim usability for any and every job.
WordPress, plug-ins, and high-stakes environments: a mismatch waiting to happen
WordPress powers a vast proportion of the web, including for some extremely well-known organisations. It has undoubtedly been a key tool in the propagation of the contemporary internet and in the right place, for the right job, with the right support, it can perform well.
It is flexible, still seemingly “open-source”, and supposedly easy to staff and support via a rich ecosystem of plugins and hosting providers. For blogs, marketing sites and general communications, it is often an entirely reasonable choice.
But the OBR incident underlines a hard truth that many organisations prefer not to confront – WordPress was never designed for mission-critical, time-sensitive publishing. Those using it often find that “free” comes at an eye-watering cost, and “open-source” brings a level of business risk unrecognised until it blows up in their faces.
A basic security scan this week (conducted on December 2nd) of the OBR site using an official WP scanning tool, wp-scan, shows that six days after the Budget incident, the site still showed a pattern familiar to countless large WordPress deployments. On the OBR site, the listed issues shown by wp-scan include:
Third-party plugins carrying known vulnerabilities, including unauthenticated stored XSS and CSRF risks
Residual exposure through features like XML-RPC, still enabled largely for legacy compatibility
Operational attack surface created by externally accessible WP-Cron and discoverable internal structure
A reliance on plugin updates and configuration hygiene to maintain security rather than structural guarantees
None of this implies negligence. In fact, the OBR’s WordPress core version is up to date, the hosting stack is modern, and the site is maintained by competent professionals who had well-understood processes in place to prevent the very thing that happened. From what we can see in the report, they deserve no flak at all.
And that is the actual point.
Even well-run WordPress installations inherit systemic risk because the platform optimises for extensibility, not containment. Security is hard to maintain because of the very things which make WordPress attractive and “cheap” in the first place - plugins. The publishing tools are pretty basic until you invest in building the sort of tools that publishers need, using plugins and developer graft. And if you are building those tools, congratulations, you are now in the building-a-CMS game, and you will already know it is neither free or easy.
Publishing is much more than just content management
For organisations handling market-making data, regulatory disclosures, or government communications, publishing is not a CMS problem. It is a control problem.
Enterprises need to be able to say with certainty:
This document cannot be accessed before a specific point in time
There is no alternate URL, API endpoint or cached variant which bypasses access controls
Security does not depend on every plugin being configured perfectly and working only as expected
Failure modes are closed by default, not open
WordPress does not fail because it is poorly engineered. It is excellent at doing what it was actually built for, and it fails because it was never intended to solve this class of problem, at least not without major investment and commitment to its upkeep.
Retrofitting enterprise publishing requirements onto a general-purpose CMS is like installing vault doors in a garden shed. You can add locks and alarms and spend big on guards and fluorescent jackets, but the structure underneath still dictates your risk. All the seemingly boring, yet best-practice features that specialised platforms provide are rarely valued, until mistakes happen.
Empathy first, architecture second
It is important to stress again that incidents like this are rarely caused by bad people or bad teams. They are caused by reasonable decisions made within constraining assumptions, by people attempting to do the right thing. In aviation terms, it is called the Swiss cheese scenario - no single problem in a chain of events leading to an accident could cause the accident. But when all the holes all line up...
WordPress is familiar. It strenuously bills itself as being cheap. It appears secure when well maintained and without any plugins. It has been “good enough” before in many a publishing career.
But “good enough” is a dangerous standard when failure carries national, financial, or reputational consequences.
The OBR’s situation is not unique. Similar issues have occurred across government, finance, healthcare and regulated industries worldwide. The platform is not always the same - WordPress has many open source alternatives - but the ethos that lead to the scenario often is.
What enterprise publishing should look like
None of this is to suggest that enterprise platforms are flawless. They come with a cost and complexity which require organisational commitment to use properly, and in his report, independent expert Professor Ciaran Martin sums it up thus: “...content management systems, like other key systems, will not function as intended if they are not configured absolutely correctly”.
But as stated above, there is a philosophy of architecture and diligence which should guard against even those errors. Specialist systems should not ‘fail open’, allow content to be released before authorised, or leave timing and access controls dependent on manual processes.
A proper enterprise publishing platform treats content release as a controlled operation, not a page update.
That means:
Hard, non-bypassable publication controls enforced at the platform level
No public access surfaces unless explicitly enabled
Separation between content preparation and content delivery
Minimal dependency on third-party extensions for core security guarantees
Auditability that does not rely on web server logs or luck
This is not about gold-plating or vendor snobbery, but rather boringly, is about aligning tooling with risk and consequence. Basically, will the fundamentals of your chosen system lead to what has been described as the worst failing in your organisation’s history? The ex-Chair of the OBR may well be asking himself that very question right now, and I have real sympathy for him.
A quiet lesson worth learning
The OBR incident was not anomalous, and it certainly was not due to a security breach. Content became publicly accessible prematurely because the workflow and publication controls were insufficient for a mission-critical release. The root cause was structural: the platform was not designed to enforce strict timing and access controls because, at its core, it lacks sophisticated, publisher-grade best practices. You have to build them yourself - that is the WordPress bargain.
Publishing has more than its own knowledge of this. Our periodic scans of WordPress-powered publisher and media sites reveal a similar recurring pattern resonant of the OBR incident, rather than it being a one-off.
This week, we tested 117 publisher and media sites against the latest version of WordPress, 6.8.3, released on September 30th. (Version 6.9 actually launched this week, but that doesn’t affect our findings). Of those 117 sites, two months into the new version:
Fewer than one quarter, 29 sites, are on the latest version of WordPress
87 are on older versions of varying vintages
19 sites had well-documented security issues
While these sorts of issues did not cause the OBR incident, they do reinforce a broader lesson: “cheap and simple” platforms can look fine right up until a basic workflow or business-critical process fails, causing reputational, financial, or operational harm.
They also don’t maintain themselves. Yes, the OBR site is on the latest version of WordPress, but it still has out-of-date plugins and some vulnerabilities.
Organisations like the OBR, constrained in budget and staffing, don’t see themselves as publishers. However they absolutely need robust publishing controls. This is not a failure of people: it is a structural limitation of using a general purpose CMS for high-stakes content, and assuming risk has been removed by plugins and DIY.
For low-risk publishing, WordPress continues to be an excellent tool, and we would be one of the first to recommend it - even as it seems to be suffering its own crisis of identity.
However for time-sensitive, confidential, or high-trust communications and publishing, it is self-evident that specialised platforms are the necessary choice.
Choosing the right tool for the job is not controversial; don’t set up your teams to fail.
Versus verses
AI models fooled by rhyme, words concealing tricks each time. In coded lines, a secret spun, Italian boffins show it done. “Adversarial poetry,” they dub such plays, unpicking bots in clever ways. A sneak attack with clever pun, could be your hacker’s smoking gun!
Read
Zuck in a muck
Swedish media groups are taking Meta to court over scam ads on Facebook and Instagram which impersonate journalists. Swedish media body Utgivarna says the ads exploit media brands and their staff, and cause financial and psychological harm to the faked journalists and scammed users seeing the ads despite repeated efforts from media to get them removed. Meta, recently revealed by its own estimates to have made $16bn in 2024 from the 15 billion dodgy ads per day users see, says that fighting scams is a “top priority”.
Read
Legal reality checks
The legal system is throwing many a wrench into the AI industry’s gears, but why do seemingly similar cases take such different turns in rulings? Recent outcomes of suits in the UK and Germany highlighted the subtle differences in direction judges can take in cases, notwithstanding the different jurisdictions involved. Even within the EU, cases have and will go different ways dependant on local interpretations of law.
Read
“Are ya winning?”
Meanwhile as multiple AI legal actions stack up in courts around the world, Press Gazette AI hawk Charlotte Tobitt has kicked off a rolling monitor rounding up all the twists, turns, and legal drama for you to bookmark. This is in addition to the title’s ongoing monitor of who is suing, who is doing deals.
Read
EU pause sparks compliance headaches
EU regulatory whiplash, again. The bloc has paused parts of the EU AI Act to help companies catch-up with the regs, but critics bemoan it means 16 months of uncertainty with no guarantee current plans won’t end up being the requirement. What was supposed to be a helping hand to aid industry has turned into a mess, leaving countless businesses and industries unsure whether to push ahead with compliance efforts or stand down and wait.
Read
Screen-time showdown
Australia’s social media ban for under 16’s kicks in next week (Dec 10), and the message to platforms is obey or face consequences. Social media firms will have to take “reasonable steps” to make sure kids aren’t on their sites. The law itself has sparked a mix of admiration and criticism, worry that enforcement will be impossible, and already counter actions in court by teenagers. According to the Australian Communications Minister, this is only the first step in an evolution by Governments to online risks of all kinds. Everyone is taking notes.
Read
Journalists 1, AI 0
AI gets no free pass in the Politico newsroom, as unionised journalists win a landmark arbitration ruling that new AI tools breached contracts. The ruling says new AI tools violated both bargaining rules and journalistic standards, giving Politico 60 days to negotiate or fix.
Read
Discovery phase
Google will tell you misleading headlines is not good for users - but that isn’t stopping it from using its own (assumedly cheapest) AI to rewrite yours and fill them with lies. Google AI-generated headlines and summaries are appearing into Discover, with the occasional mangling of facts as bonus. It’s being brushed off as a growing pain. But there’s more! AI Mode is moving in for a co-starring role on mobile Search too, pushing publishers another step further away from users.
Read
Brothers in arms
The News/Media Alliance has jumped into Thomson Reuters’s legal fight with Ross Intelligence, where it is arguing that Ross built an AI assistant by copying Westlaw, Reuters’s own legal research tool. The Alliance has warned that if the court green lights this kind of “copy now, innovate later” approach, publishers’ burgeoning business of licensing content to AI could get rolled over in the process. Read the full brief here [PDF].
Read
Fake websites, real AI ambitions
Silicon Valley is set on training AI to use websites and carry out actions, and the small matter of being blocked from websites isn’t deterring them. The current hot dev ticket in Silicon Valley is building fully working fake versions of sites of major brands and destinations, including Amazon, Gmail, retail and travel sites, and more. They look almost identical - some have even used official logos - with “working” buttons, menus, and such, so AI agents can treat them like school and learn to shop, book flights, and manage tasks. Even though logos are usually different, legal experts believe these are still skating on thin (copyright) ice. The unusual thing is them being made public.
Read
Calling Content Aware readers in the Middle East
Glide’s leadership team will be at the Bridge Summit in Abu Dhabi next week, December 8-10 at the ADNEC Centre, to talk about modern media, audience engagement, and the ways AI can safely springboard content and revenues.
Want to speak to us? Come and see us, or drop us a line here.